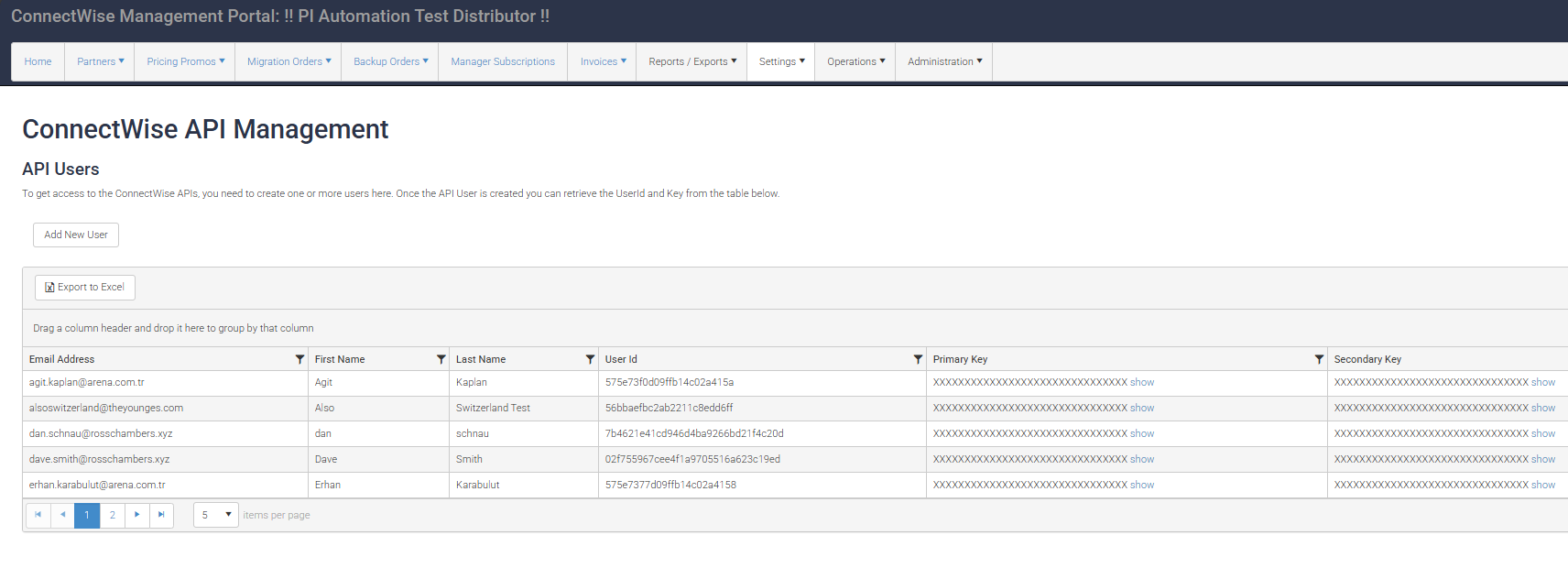
Important Note: Always treat a user’s subscription key as sensitive information. It shouldn’t be shared via insecure means such as email, http, etc. or included in client-side code (javascript).
Generating an Authentication Request
When requesting an access token from the authentication operation there are a few pieces of information that must be provided.
The token endpoint requires a Basic Authorization header where the username is the user’s API user ID and the password is the user’s subscription key (either the Primary or Secondary will work). The endpoint also requires a Ocp-Apim-Subscription-Key custom header where the value is the user’s subscription key. The final header required header is a Content-type header and the value must be set as application/x-www-form-urlencoded.
The request body should be of the format grant_type=client_credentials&scope={Product} where {Product} can be replaced with whichever product you’re attempting to use (usually Partner or Distributor).
Receiving an Authentication Response
As a part of the response we include the access_token, which is the bearer token that will be used for future API calls. The other part of the response is the expires_in value, which indicates how long the token is valid for.
Token Caching and Reuse
It’s important to cache and reuse the token received from the API response. There are several reasons for this.
The API has strict rate limits on the auth operation, if too many requests are made in too short of a span the requests will fail.
If prior to every API call, a new bearer token is being received, the application will have a significant degradation of performance.
Using an Access Token
The bearer token will be used on all other API calls. This can be done by including the Authorization header with the value Bearer {BearerToken}, where {BearerToken} will be replaced with the access token. The request must also have the custom header Ocp-Apim-Subscription-Key with the value being a valid subscription key.
Samples
Getting an Access Token
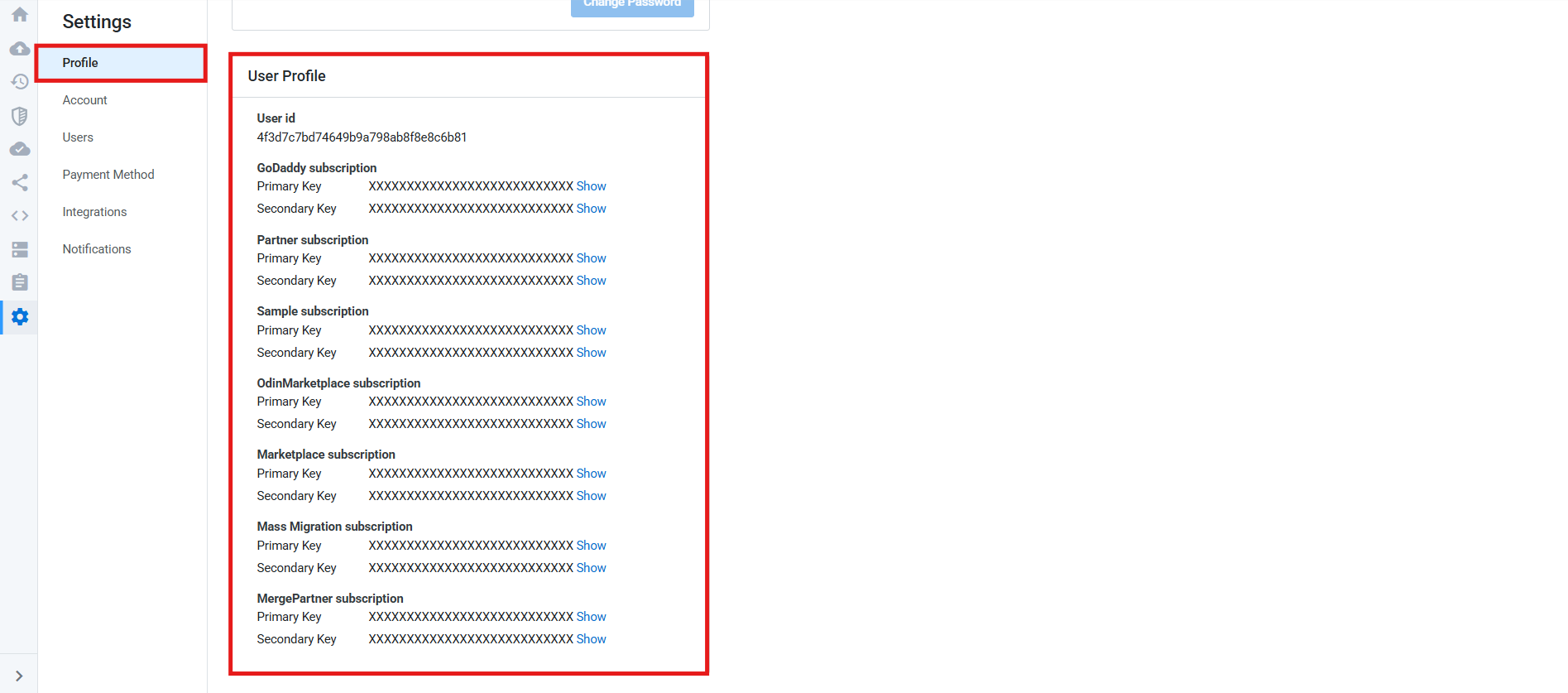
Assume user ID4f3d7c7bd74649b9a798ab8f8e8c6b81and subscription key 1476aca794464056ba8aa6a1a9f921da
Concatenate user ID and subscription key with a colon 4f3d7c7bd74649b9a798ab8f8e8c6b81:1476aca794464056ba8aa6a1a9f921da
Base-64 encode it NGYzZDdjN2JkNzQ2NDliOWE3OThhYjhmOGU4YzZiODE6MTQ3NmFjYTc5NDQ2NDA1NmJhOGFhNmExYTlmOTIxZGE=
Use the encoded value in the Authorization header Basic NGYzZDdjN2JkNzQ2NDliOWE3OThhYjhmOGU4YzZiODE6MTQ3NmFjYTc5NDQ2NDA1NmJhOGFhNmExYTlmOTIxZGE=
Example Response:
{
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIn...Zd7YOBcBowYV7tQNPloUAQNtjo93lBPLJV1whe2ndHA",
"expires_in": 3600,
"token_type": "Bearer"
}Using an Access Token
In order to use the bearer token obtained using the steps above, do the following:
Add Authorization header with value Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIn...Zd7YOBcBowYV7tQNPloUAQNtjo93lBPLJV1whe2ndHA
Add Ocp-Apim-Subscription-Key header with the value 1476aca794464056ba8aa6a1a9f921da.
The body of the request would depend on the operation being used.
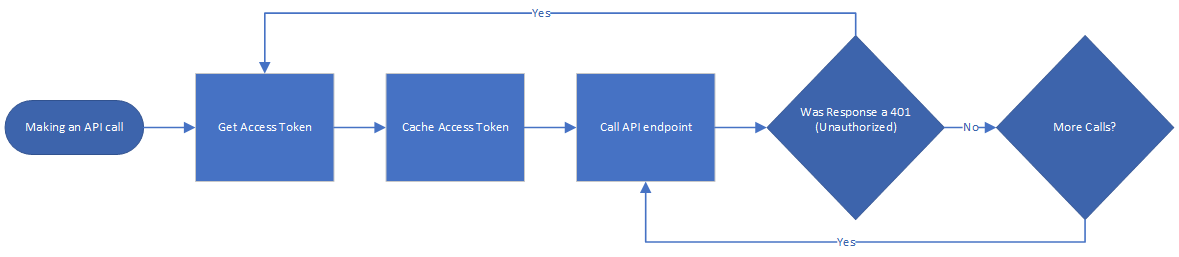
Workflow